Description of the problem
In your company you have an internal URL for a server, for instance: myserver1.yourcompany.com. It means you have an entry for myserver1.yourcompany.com in your DNS server dns1.yourcompany.com.
You also want to expose publicly this URL to customers in order they test your application/service. Then you have a DNS entry for myserver1.yourcompany.com in a public DNS like gandi.net.
Now some of your IT employees connect via ssh to myserver1.yourcompany.com, but when they use their VPN they can’t. After having a quick look (nslookup), you see that when they use their VPN it’s not dns1.yourcompany.com that is used to resolve the server IP but a public DNS.
DNS leak and transparent proxy
Two reasons:
- DNS leak
- Transparent proxy
In your VPN configuration you should have specified which DNS servers you want expose to your users. For instance:
- 1/ dns1.yourcompany.com
- 2/ 8.8.8.8 (google DNS)
It means firstly your DNS server, and if no corresponding DNS entry found, then Google DNS servers. That’s all.
DNS leak
Now do a DNS leak test for example with dnsleaktest.com which an online DNS leak tester.
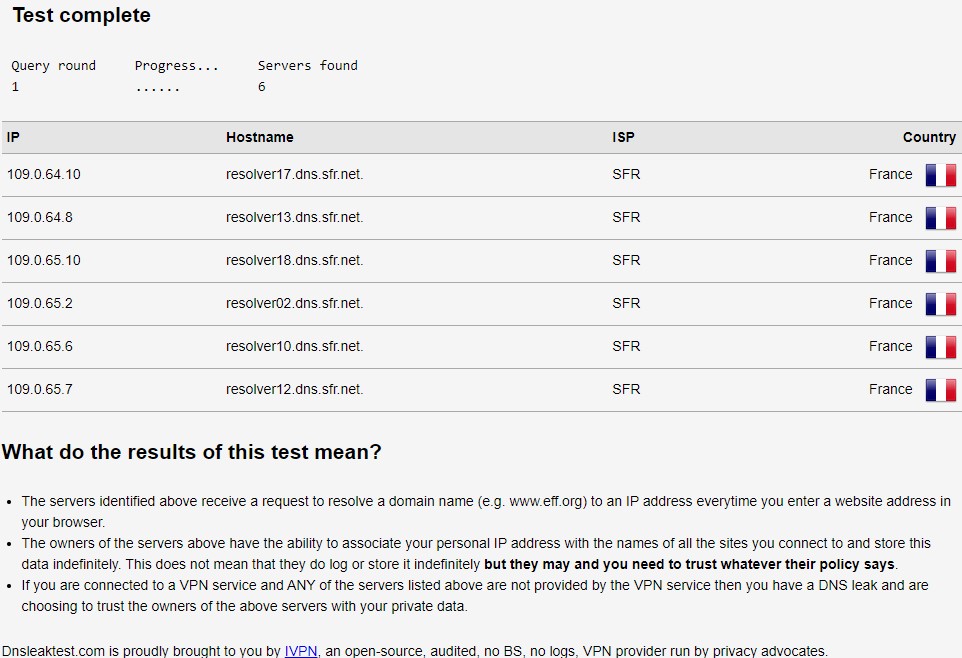
Here you can see a DNS leak, it means you DNS lookups use DNS servers that are not provided by your VPN. And here these DNS are the ISP DNS servers (it is often like this, the ISP intercept all your DNS queries and it means your browsing with your VPN is not so private).
OK this just offend your privacy.
Transparent DNS proxy
But it you execute an nslookup command for an internal URL/server of your company and the result is “unknown host” instead of dns1.yourcompany.com, it means that your ISP has proxy the result of your DNS query and has forced you to use their DNS servers without your knowledge. That is transparent DNS proxy.
It means that instead of serving you the result of your DNS query with your company DNS they used first their DNS server, find a result then sent you the result.
If they hadn’t find a DNS result with their DNS server they would have queried your dns server and it would have been fine for you.
It is important to note that not all ISP will do transparent proxying it really depends of the ISP. That also explain why for some of your IT collegues using the VPN there is no problem, and for others there is.
Solution: block outside traffic with your VPN
In the case of OpenVPN you simply have to add the following two lines to ensure there is no more DNS leaks, and it also means no more transparent proxy:
ignore-unknown-option block-outside-dns
block-outside-dnsYou should put these two lines just before the <ca> tag:
...
auth-user-pass
remote-cert-tls server
ignore-unknown-option block-outside-dns
block-outside-dns
<ca>
...Now verify that you don’t have anymore DNS leak (and then no more transparent proxy):
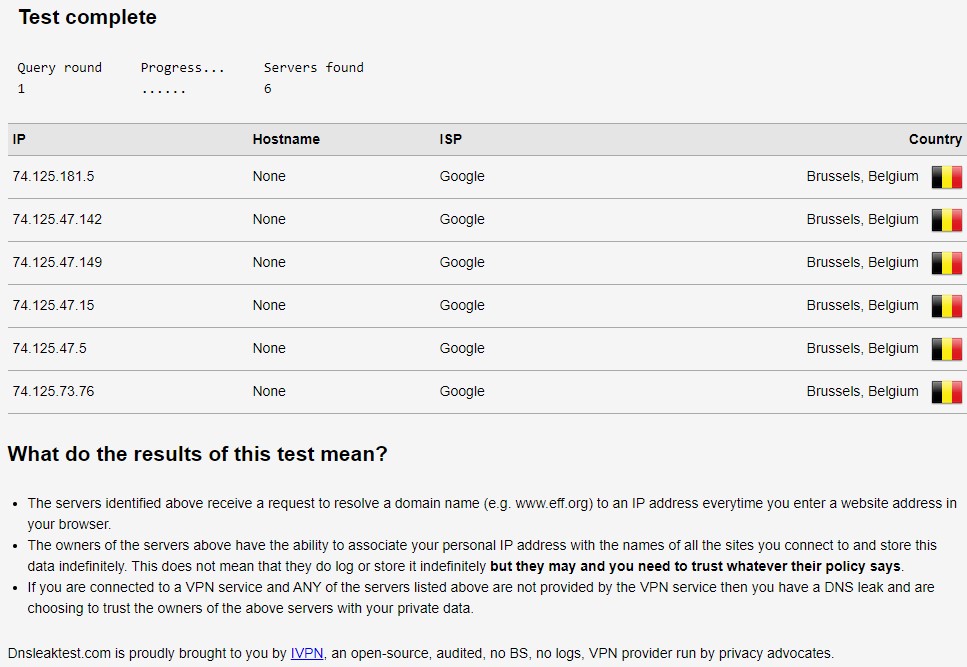
As you can see, now only Google DNS servers are used to resolve external URL.

Leave a Reply